Forensic Software Utility
The CRU Forensic Software Utility provides an easy-to-use method to interact with and validate functionality of various CRU WiebeTech forensic products and drive docks.
FEATURES
- View drive info
- View write-blocker info
- Save info to a log file
- Check for available product firmware updates
- Verify that write-blockers for USB devices has not been tampered with (via hash of the firmware itself)
- Configure default behavior when encountering HPA/DCO areas on drives
- Verify write-blocking capability of CRU forensic products
VIEW INFO
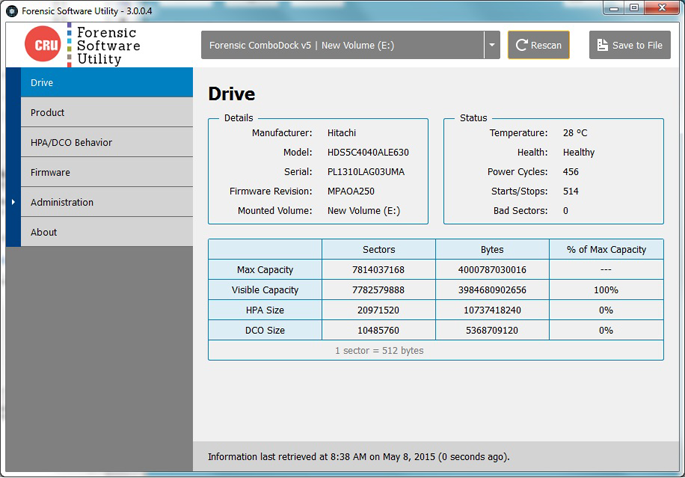
After a CRU Dock is connected, you can view information both about the Dock itself, as well as the attached drive. Model and serial number information is available, and can be saved with the “save info…” button. Files can be saved in either text or HTML format.
Forensic Software Utility (for 64-bit versions of Windows)
Download: ForensicSoftwareUtility-3.2.0.11-x64.exe (7.3 MB)MD5: 380829abf8524e7b35fc77cc92b5f845
Sha256: 4870bb6a75d4399ed6bd44d038333acb29374620dd40922c3b791ff15c8099a7
Forensic Software Utility(for 32-bit versions of Windows)
Download: ForensicSoftwareUtility-3.2.0.11-x86.exe (6.1 MB)MD5: 9f80da589bdb5abda086bc342449393c
Sha256: b137f1fb55117f2e537bb1adec2540149a808a82d89d458679ae235a939153a8
CHECK FOR FIRMWARE UPDATES
CRU occasionally updates firmware for forensic products to add new features or enhance compatibility with the FSU application. FSU can show you the current firmware version on attached products and notify you if a newer firmware version is available. Note: a separate app, CRU Configurator 4.0 for Windows, is needed to perform the firmware update.
FIRMWARE HASH CALCULATION
This special feature is available for write-blockers designed for USB devices: USB WriteBlocker, Media WriteBlocker, and USB DataDiode. Although these products cannot be reprogrammed and do not support firmware updates, FSU can offer piece of mind that the products have not had their firmware tampered with. FSU calculates a hash value for the firmware on the product and reports whether the hash matches known-good values.
HPA/DCO MODES
Nearly all CRU forensic products look for and identify hidden areas on hard drives called HPA or DCO. How the products handle such areas is then up to you. There are four ways for a write-blocker to handle HPA or DCO areas:
- Detect and report, but leave them in place
- Detect and temporarily bypass HPA
- Detect and permanently unhide HPA
- Detect and permanently unhide any HPA and DCO
CRU forensic products with LCDs allow you to select from these options on-the-fly. Products without LCDs can be configured via FSU to use your preferred HPA/DCO mode. By default, such products will only detect and indicate the presence of HPA/DCO areas, but not unhide them.
VERIFY WRITE-BLOCKING CAPABILITY
It’s standard practice to test write-blockers before using them to access sensitive data. FSU 3.0 includes an automated test to simplify this process. With the click of a button, FSU will perform the following steps to verify that a product is properly blocking writes to attached drives:
- Attempts to write a test file to the drive
- Temporarily dismounts the drive
- Remounts the drive
- Reads the drive to check for the presence of the test file
- Displays a pass/fail message
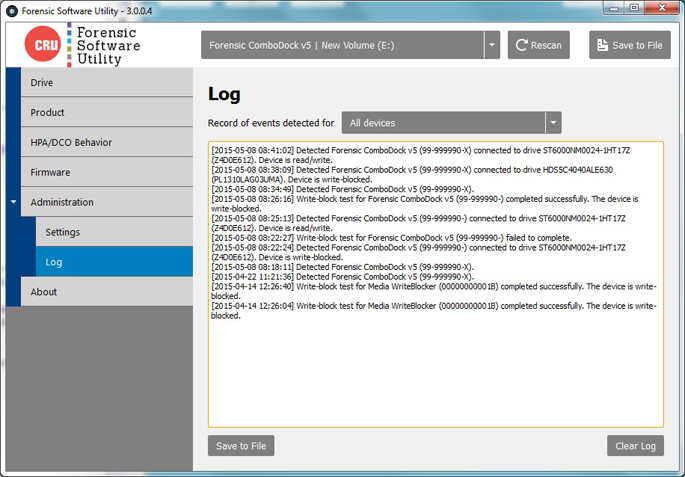
EVENT LOGGING
FSU maintains a log as various events are detected for later review. Log entries can be filtered by device. The following events are logged:
- Device detection – once per session unless the device is disconnected then reattached
- HPA/DCO setting changed on a product
- Firmware changed – if a product’s firmware is determined to be different than what was previously detected
- Firmware hash calculated
- Write-block test performed