DATA ENCRYPTION AND STORAGE ENCLOSURES
 CRU uses the term “encryption” to mean protecting and securing a hard disk drive or SSD, and the data that resides on that drive.
CRU uses the term “encryption” to mean protecting and securing a hard disk drive or SSD, and the data that resides on that drive.
Many of our customers are required to secure their data, due to government regulations, risk assessment, or potential liabilities. Others want to simply keep their personal or business data safe from prying eyes.
 Encryption inside
Encryption inside
There are different methods to encrypt data, beginning with the choice of using specialized hardware or software designed to protect data at various security levels. CRU makes hard drive enclosures that include an encryption engine, giving the drive enclosure the built-in ability to encrypt the entire disk(s) in the enclosure. (And in turn, read the drives it encrypted.) Encrypted CRU drive enclosure products generally contain the word “Secure” in the product name. With a CRU Secure drive enclosure, you don’t need additional encryption software on your computer. When used with a CRU Secure enclosure, no additional or specialized formatting of the disk is needed; the disk is essentially “locked down” and unreadable unless it is in the enclosure and the proper physical key is inserted.
A CRU Secure enclosure comes with physical keys that are specific to that enclosure. The keys are programmed with random multi-bit codes that meet the National Institute of Standards FIPS 140-2 Security Requirements. One of these physical keys needs to be inserted into the enclosure before the host computer can read the data on those disks. This level of protection makes it essentially impossible to hack into the drive.
Why would you need, or want to, encrypt your data?
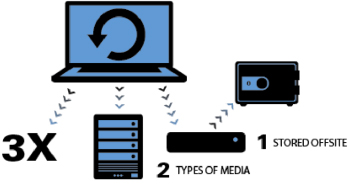 Sensitive organizational, business, client, or personal data exists on the computers in your organization. When you practice the recommended 3-2-1 backup strategy, backup drives will go offsite as part of your disaster recovery plan. You’ll want these drives to be protected just like the data inside the four walls of your organization. By encrypting all of your disks, the offsite drives are unreadable by anyone who’s unauthorized to read the drives should they be misplaced or stolen.
Sensitive organizational, business, client, or personal data exists on the computers in your organization. When you practice the recommended 3-2-1 backup strategy, backup drives will go offsite as part of your disaster recovery plan. You’ll want these drives to be protected just like the data inside the four walls of your organization. By encrypting all of your disks, the offsite drives are unreadable by anyone who’s unauthorized to read the drives should they be misplaced or stolen.
Encryption Keys and AES
For more information about how CRU uses physical encryption keys with its products, how you can program these keys, as well as how safe your data is when encrypted by a CRU Secure enclosure, see below.
 CRU Secure Encrypted Products
CRU Secure Encrypted Products
CRU carries a full line of secure storage enclosures and accessories to keep your data safe from prying eyes. To find a product to help you protect your data, start here.
Many CRU drive enclosure products are available in configurations that offer the ability to secure disk drives from unauthorized reading or access with encryption that meets the US National Institute Standards and Technology (NIST) Advanced Encryption Standard (AES).
Strong, total disk, real time hardware encryption
Data is encrypted in real time, in the enclosure hardware, completely independent of the host computer’s operating system. A physical key (dongle) is used in the enclosure to authorize encryption, decryption, and access. Only those who have the correct key may access the contents of an encrypted drive. (Note that CRU Secure products ship with multiple keys for redundancy. Keep one in a safe place since if all keys are lost, any drives encrypted by the enclosure will be unreadable.)
Benefits of the CRU physical key-based hardware approach to encryption include:
- Independent of operating system type
- Hardware-encrypted in real time
- No passwords
- 100% of the drive is encrypted (including information like file allocation tables)
- More secure than software encryption
- AES 256 is recognized by the government. It’s so strong that there are restrictions to what countries we can sell to.
Easy, Automatic Encryption
Encryption is performed automatically by the real-time encryption engine built into circuitry in CRU Secure drive enclosures. When connected properly and the physical key is in place, your computer sees the drive volume available as a normal full-speed drive. If your drive is lost or stolen, however, you can rest assured that without the proper physical AES encryption key, no one will be able to view its contents, as the drive appears to an operating system as an empty, unformatted drive.
How to use CRU AES encryption keys
- Connect the Secure enclosure to your computer via USB 3.0/2.0, FireWire, or eSATA.
- Insert your AES Encryption Key.
- Power on the enclosure.
- Wait for the green encryption LED to light up on the bezel of the product (look for a key icon labeled AES). The green light confirms the key is accepted.
- You can now remove the AES Encryption Key. It’s not needed again until the power is cycled.
The ability to remove the key after power up helps you keep your physical key safe. The key is smaller than a standard thumb drive and easily fits on a key chain or lanyard.
AES Encryption Keys
Your encrypted product generally ships with 3 identical keys (some other configurations may be available). These three keys exist so you can
- Keep one with you (for your own use)
- Keep a backup on site in a safe location
- Keep a backup off site in a safe location
These keys will be completely unique to you. There are 2128 or 2256 (depending on encryption strength) possible ways to encode a key. If one of your keys is compromised, via theft or loss, you should consider replacing your keyset so that the lost key could never be used by someone else to unlock your data.
|
How big is 2128? 2128 = 340,282,366,920,938,463,463,374,607,431,768,211,456 |
| This is how many unique encryption keys can exist for 128 bit encryption. |
| How big is 2256? 2256 = 115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564, 039,457,584,007,913,129,639,936 |
| This is how many unique encryption keys can exist for 256 bit encryption. |
How safe does this make you against an attacker?
A full-on attack to locate your secret key would require an exhaustive search. “Brute force” cypher-cracking software uses code that would cycle through each key. At each and every possible key, it would perform a check to see if data is readable (this check takes time). Even if a computer can check millions of keys per second, 256 bit encryption would take 3.67×10^60 years to check each key. Far beyond our computational abilities.
But what if someone had a billion computers working on it together, each checking a billion keys per second?
One billion is about three times the US population, so each US citizen would need to pitch in three supercomputers to this project (each computer being thousands of times more powerful than we have today). Even then, it would take these computers 3.67×10^49 years to exhaust the keyspace. If you don’t like scientific notation, that’s 36,720,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000 years.
To put that awfully big number of years into perspective, consider the universe is thought to be only 13,700,000,000 years old.
Does the US government recognize this strength?
Yes – our implementation of 128 bit encryption is FIPS-197 listed (certification number 60). Our implementation of 256 bit encryption has been validated to FIPS 140-2 (certification number 1471).
For your convenience, we offer replacement pre-programmed key sets, which contain unique encryption keys.

